Example - PIN
This is a walkthrough of how to use PIN as an authentication method for SCA including setting it up for your end customers.
Please note that all PIN-related endpoints use Jose direct encryption for secure data encryption in transit. It is essential to never persist this sensitive data in your application and only retrieve it directly from the customer
Create PIN API allow customers to setup their PIN with Wise directly.
This will allow customers to send their desired PIN to Wise in a direct encrypted manner which not even Wise will know about its value.
Once an end customer's PIN is set up. It can now be used as an authentication factor to clear an SCA challenge.
Image below illustrates the interaction between Partner and Wise.
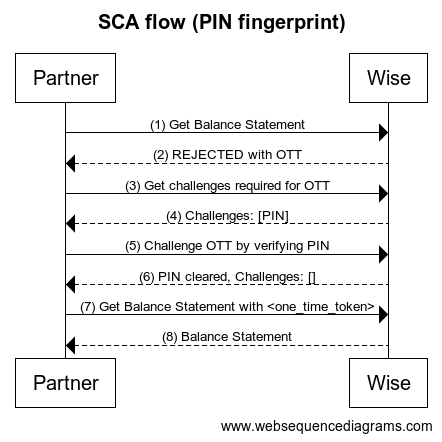
Steps
- Partner makes an HTTP call to get balance account statement which is a SCA protected endpoint.
curl -X GET https://api.sandbox.transferwise.tech/v1/profiles/{{profileId}}/balance-statements/{{balanceId}}/statement.json \?currency=EUR \&intervalStart=2023-01-01T00:00:00.000Z \&intervalEnd=2023-01-15T23:59:59.999Z \&type=COMPACT \-H 'Authorization: Bearer <your api token>'
- Wise rejects the request with status 403 Forbidden. Please see the example response on the right.
HTTP/1.1 403 ForbiddenDate: Wed, 06 Dec 2023 08:57:34 GMTx-2fa-approval: bb676aeb-7c4d-4930-bb55-ab949fd3fd87x-2fa-approval-result: REJECTED...other headers
- Partner gets status of a one time token to get all required challenges to clear this OTT.
curl -X GET https://api.sandbox.transferwise.tech/v1/identity/one-time-token/status \-H 'Authorization: Bearer <your api token>' \-H 'One-Time-Token: bb676aeb-7c4d-4930-bb55-ab949fd3fd87'
Wise returns one time token that describes all required challenges.
For the complete list of challenges available please refer to ChallengeType.
{"oneTimeTokenProperties": {"oneTimeToken": "bb676aeb-7c4d-4930-bb55-ab949fd3fd87","challenges": [{"primaryChallenge": {"type": "PIN","viewData": {"attributes": {"userId": 6146956}}},"alternatives": [],"required": true,"passed": false}],"validity": 3600,"actionType": "BALANCE__GET_STATEMENT","userId": 6146956}}
- Partner verify PIN by passing OTT acquired in step 2.
curl -X POST https://api.sandbox.transferwise.tech/v1/one-time-token/pin/verify \-H 'Authorization: Bearer <your api token>' \-H 'Accept: application/jose+json' \-H 'Accept-Encoding: identity' \-H 'Content-Type: application/jose+json' \-H 'Content-Encoding: identity' \-H 'X-TW-JOSE-Method: jwe' \-H 'One-Time-Token: <one time token>'-d 'eyJlbmMiOiJBMjU2R0NNIiwi...'
- Wise returns one time token properties after a successful pin verification.
Assuming that the challenges array field is empty, indicating that the OTT is now usable.
If you are unsure, you can always get status of a one time token again.
It is possible that the challenges array returns type of challenge. In that case, please perform the verification flow as written in our guides.
eyJlbmMiOiJBMjU2R0NNIiwi...
- Partner calls Get Balance Statement with the approved OTT.
curl -X GET https://api.sandbox.transferwise.tech/v1/profiles/{{profileId}}/balance-statements/{{balanceId}}/statement.json \?currency=EUR \&intervalStart=2023-01-01T00:00:00.000Z \&intervalEnd=2023-01-15T23:59:59.999Z \&type=COMPACT \-H 'Authorization: Bearer <your api token>' \-H 'x-2fa-approval: bb676aeb-7c4d-4930-bb55-ab949fd3fd87'
- Wise returns Balance Account Statement.
{"accountHolder": {"type": "PERSONAL","address": {"addressFirstLine": "Veerenni 24","city": "Tallinn","postCode": "12112","stateCode": "","countryName": "Estonia"},"firstName": "Oliver","lastName": "Wilson"},"otherFields": "..."}